Introduction
Laravel Cloud manages all aspects of networking in order to bring enterprise-grade speed, security, and scalability to any Laravel application. There are two main layers to the Cloud’s networking infrastructure: the Cloud Edge Network and the Cloud Compute Network.Cloud edge network
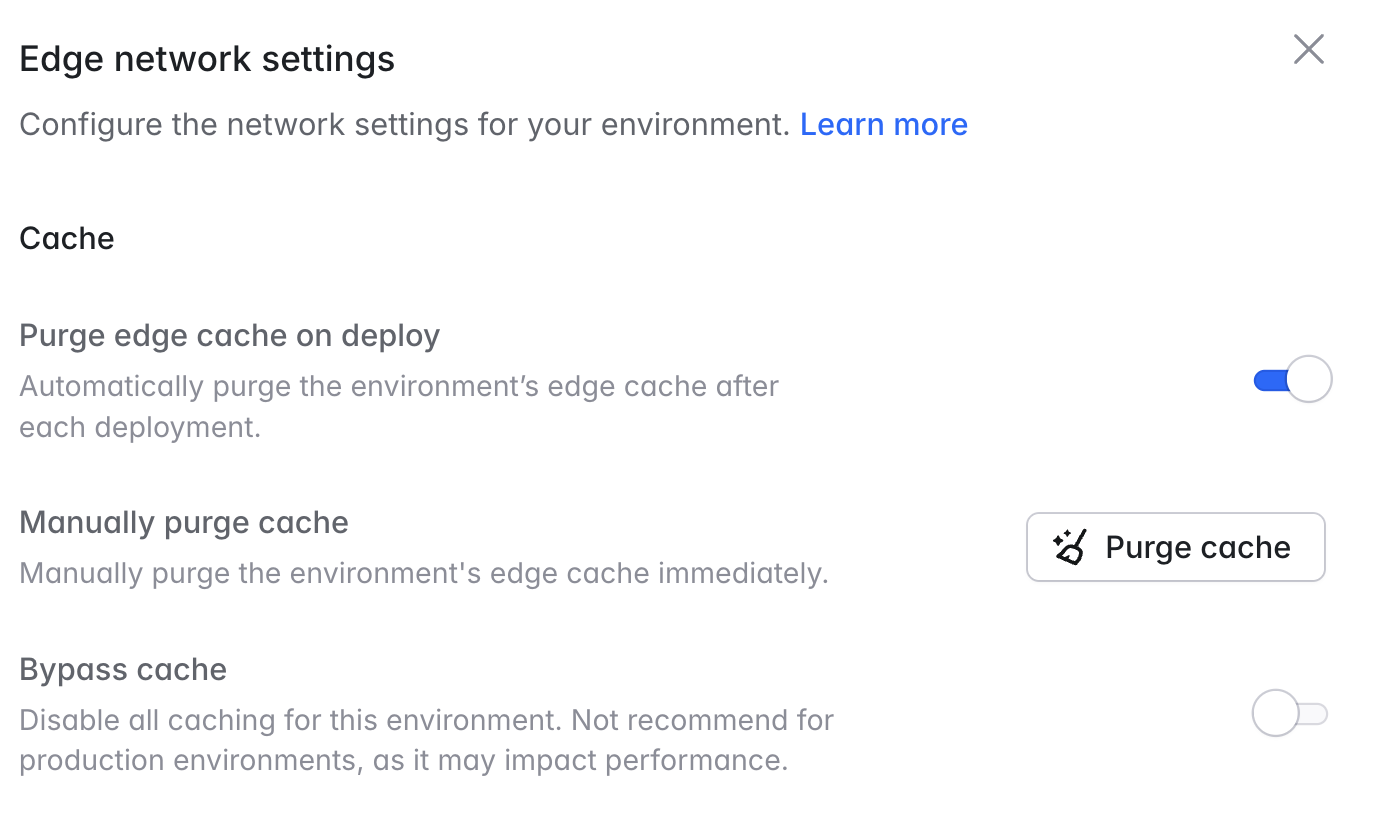
Laravel Cloud has partnered with Cloudflare to offer every application globally distributed caching and network security at the edge. Incoming HTTP requests are first routed to the nearest edge region (335 cities around the world), pass through DDoS mitigation and Web Application Firewall (WAF) security layers, and are either returned from the cache (if available) or passed on to the Cloud Compute Network to be routed to your application’s compute cluster.Cache control
An important function of the Cloud Edge Network is caching your application’s static assets. This has two key benefits: it reduces the number of requests that your application’s compute needs to handle and it decreases latency for your users. Laravel Cloud optimizes your CDN cache through a two-step approach. First, Cloud uses a long cache lifespan to ensure your static assets are served at the edge as much as possible. Second, Cloud clears the CDN cache automatically on every deployment to ensure that no stale files accidentally remain in the cache. Combined, these two steps offer an efficient and safe approach to CDN caching. By default, Laravel Cloud caches files with the following extensions:7Z, APK, AVI, AVIF, BIN, BMP, BZ2, CLASS, CSS, CSV, DMG, DOC, DOCX, EJS, EOT, EPS, EXE, FLAC, GIF, GZ, ICO, ISO, JAR, JPEG, JPG, JS, MID, MIDI, MKV, MP3, MP4, OGG, OTF, PDF, PICT, PLS, PNG, PPT, PPTX, PS, RAR, SVG, SVGZ, SWF, TAR, TIF, TIFF, TTF, WEBM, WEBP, WOFF, WOFF2, XLS, XLSX, ZIP, ZST
When a Cache-Control directive or Expires header is not explicitly set, Laravel Cloud will use the HTTP status code to determine the cache duration.
| HTTP Status Code | Default TTL |
|---|---|
| 200, 206, 301 | 120m |
| 302, 303 | 20m |
| 404, 410 | 3m |
Cache-Control and Expires headers in your application code. Laravel Cloud will respect these headers and cache your assets according to the rules you set.
Certain headers set by your application can prevent Laravel Cloud from caching a response.
- The
Set-Cookieheader will prevent caching. - The
Authorizationheader will prevent caching (unless amust-revalidate,public, ors-maxageheader is also present).
Response rules
Laravel Cloud allows you to easily configure a number of security headers that will be set on every response. You can modify the defaults by clicking on the “Edge network” card from your environment’s canvas and selecting the desired option. You can also override the default headers by setting them directly in your application code.X-Frame-Options
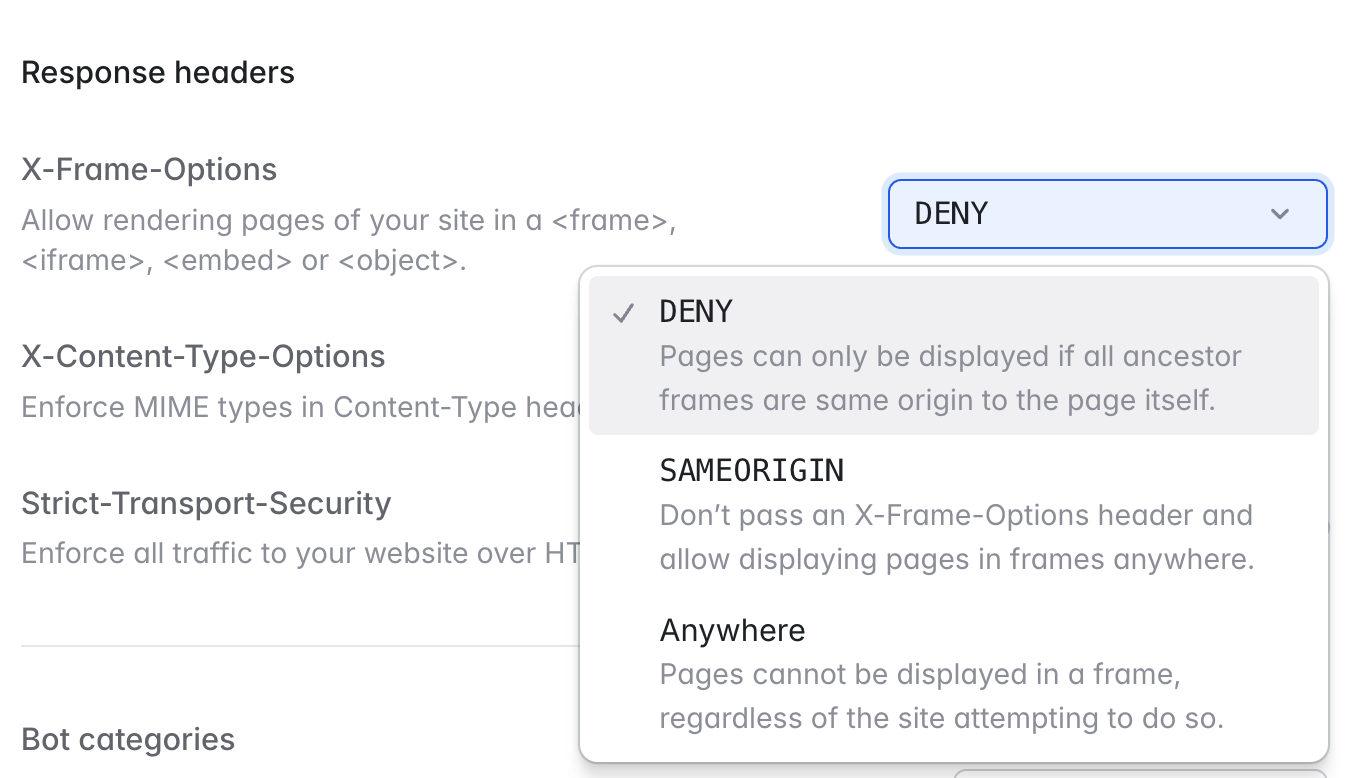
By default, Laravel Cloud will set anX-Frame-Options: DENY header. This prevents certain types of attacks that can occur if an application is loaded from an iframe. If your application has a use case for allowing iframes, you can change the header value to SAMEORIGIN or you can unset it entirely by clicking “Edge network” from the environment’s canvas.
X-Content-Type-Options
By default, Laravel Cloud will set anX-Content-Type-Options: nosniff header. This prevents browsers from interpreting files as a different MIME type than what is specified in the Content-Type header. This is a security measure to prevent attacks based on MIME-type confusion.
If your application has a use case for allowing browsers to interpret files as a different MIME type, you can unset the header entirely by clicking “Edge network” from the environment’s canvas and selecting “None”.
If you select the “None” option for the
X-Content-Type-Options header, your application can override the default and set a nosniff value at the route level. However, the the opposite is not true: if you select the nosniff option, your application cannot unset the value.Strict-Transport-Security
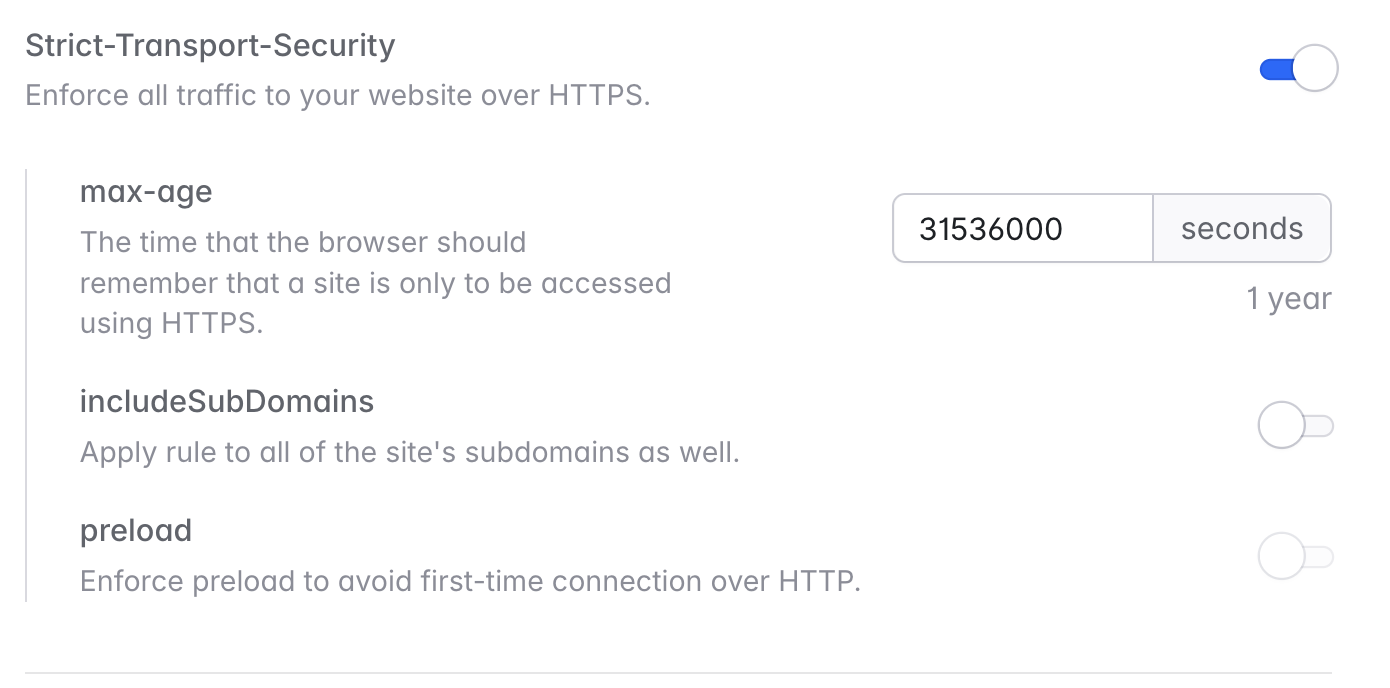
HSTS is disabled by default but can be enabled with a simple toggle. When enabled, Laravel Cloud will set aStrict-Transport-Security header with a max-age of 31536000 seconds (1 year - customizable). This header is used to enforce secure (HTTPS) connections to the server.
You can also optionally enable the includeSubDomains and preload directives. The includeSubDomains directive applies the HSTS policy to all subdomains of your application, while the preload directive allows your domain to be included in browsers’ HSTS preload lists. This means that browsers will automatically enforce HTTPS for your domain and its subdomains, even before the first request is made. Make sure you understand the implications of these directives before enabling them, as it can be difficult to remove once set due to browser caching.
X-Robots-Tag
Since Laravel Cloud domains are often used for testing and staging purposes, aX-Robots-Tag: noindex, nofollow header is automatically set on all *.laravel.cloud domains so that they are not indexed by search engines. To remove this header, you should configure a custom domain for your application. The header will not be set for custom domains.
Cloud compute network
Requests that need to be processed by your application will be routed to the Compute Network in the AWS region assigned to your Laravel Cloud application. The Cloud Compute Network is built for security and scale. Your applications run in private networks and are only made publicly accessible via the Cloud Edge Network. Compute clusters are distributed across multiple availability zones (AZs) to ensure regions remain stable and recover quickly from any interruptions in a single zone. Compute Network traffic is also intelligently load balanced across all instances in your compute cluster as you horizontally scale up or down.Web application firewall
The Web Application Firewall (WAF) provides advanced protection for your Laravel Cloud applications by filtering and monitoring HTTP traffic between your application and the Internet. All traffic routed through Laravel Cloud’s edge network, via the defaultapp.laravel.cloud hostname or a custom domain proxied through Cloudflare, runs behind Cloudflare’s OWASP Core Ruleset, giving every environment managed protection that maps to the OWASP Top 10 before traffic ever reaches your app.
Bot categories
Bot categories allow you to present a JavaScript challenge to clients identified as specific types of automated traffic. Visitors matching your selected bot categories will see a challenge before they can access your application. Categories include, but are not limited to, AI crawlers, AI assistants, advertising and marketing bots, aggregators, search engine optimization bots, social media marketing bots, and monitoring tools. You can configure bot categories by clicking on the “Edge network” card from your environment’s canvas and selecting the “Web Application Firewall” tab.Bot categories are available for Business plan customers.
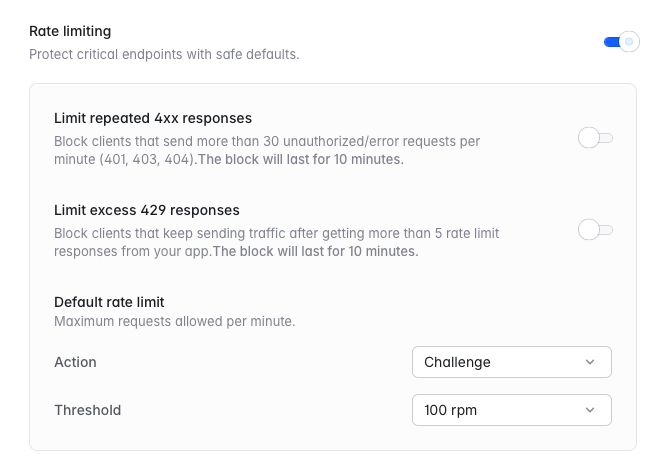
Rate limiting
Rate limiting protects your application from abuse by controlling how many requests a client can make within a given time period.Basic rate limiting
When enabled, Laravel Cloud will intercept requests from any IP address that exceeds 100 requests per minute. You can choose from three actions:- Challenge: Present a challenge (CAPTCHA or Turnstile) to the IP address. The challenge will be shown for 5 minutes.
- Throttle: Block new requests from the IP address for 5 minutes.
- Ban: Block all requests from the IP address for 5 minutes.
Basic rate limiting is available for Growth and Business plan customers.
Advanced rate limiting
Advanced rate limiting includes all basic rate limiting features plus additional customization:- Customizable threshold: Set your own requests per minute threshold instead of the default 100 rpm.
- Block repeated 4xx responses: Block clients that send more than 30 unauthorized / error requests per minute (401, 403, 404) for 10 minutes.
- Block excess 429 responses: Block clients that continue sending traffic after receiving more than 5 rate limit responses from your application. The block will last for 10 minutes.
Advanced rate limiting is available for Business plan customers.
Under attack mode
If your application is experiencing a large-scale attack or suspicious traffic spikes, you can enable “Under Attack Mode” in the Edge network settings for your environment. When activated:- All incoming traffic to your environment is filtered through additional Cloudflare security checks designed to mitigate layer 7 DDoS attacks.
- Visitors will see an interstitial “Checking your browser before accessing…” page and must pass a JavaScript challenge, which typically takes no more than 5 seconds.
- Validated users are allowed through, while suspicious or automated traffic is blocked.
- Under Attack Mode is intended as a last resort during active threats and may temporarily pause access to your site and impact your site analytics.
- This mode will automatically expire after 24 hours to ensure normal access is restored.
- Browsers must support JavaScript to pass the challenge; some third-party analytics tools may be affected.
IP addresses
Laravel Cloud applications may make outbound requests from any of the following IP addresses. This information is useful when configuring firewalls, security groups, or allowlists for external services that your application needs to access.| Region | IPv4 Addresses | IPv6 CIDR |
|---|---|---|
| US East (Ohio) | 3.135.136.57 3.149.61.67 3.20.110.34 18.220.252.20 3.140.62.214 3.139.253.68 | 2600:1f16:e0:8500::/56 |
| US East (N. Virginia) | 52.70.166.119 52.45.182.198 50.19.208.208 44.214.27.231 35.169.193.93 98.87.74.4 | 2600:1f18:124c:a900::/56 |
| Europe (Frankfurt) | 52.57.69.90 18.192.32.142 3.125.76.115 63.177.148.67 52.57.93.121 3.66.107.144 | 2a05:d014:145b:5600::/56 |
| Europe (Ireland) | 54.170.35.8 99.80.90.7 18.200.179.186 63.34.93.245 34.251.202.78 52.48.97.173 | 2a05:d018:4ce:b500::/56 |
| Europe (London) | 18.134.215.1 13.43.41.184 35.178.113.65 35.177.172.66 13.43.150.217 35.176.240.172 | 2a05:d01c:243:e500::/56 |
| Asia Pacific (Singapore) | 18.142.79.21 52.77.163.176 18.140.149.49 18.143.6.95 18.136.215.55 13.251.137.223 | 2406:da18:a1e:c100::/56 |
| Asia Pacific (Sydney) | 15.134.25.14 54.252.123.135 54.252.35.85 52.63.199.104 15.134.8.154 3.105.189.71 | 2406:da1c:9d5:3400::/56 |
| Canada (Central) | 3.97.170.94 52.60.95.142 16.52.110.200 16.54.8.67 99.79.30.160 16.52.118.51 | 2600:1f11:c23:8800::/56 |
Programmatic access
The IP addresses are also available via API for programmatic access:These IP addresses are subject to change. We recommend checking this endpoint regularly or subscribing to our changelog for updates.

